
* Following the introduction of ECM in World War II, in the postwar period the race between measure and countermeasure became increasingly tricky and demanding. This chapter provides a survey of modern electronic countermeasures technology.
* In the modern period, the development of sophisticated air defense systems with radar-guided anti-aircraft artillery (AAA) and in particular surface-to-air missiles (SAM), led to major improvements in ECM systems. In World War II, everything was done more or less manually, for example with aircrew dumping chaff packets overboard. Countermeasures receivers and active jammer systems also remained under crew control. Modern ECM systems are much more sophisticated.
There are two broad categories of ECM systems: "defensive countermeasures" systems, which are carried by an attack aircraft or other platform to prevent enemy defenses from drawing a bead on it; and "offensive countermeasures" systems, in which a dedicated ECM aircraft or other platform attempts to disrupt enemy defenses and protect air strike packages.
* A modern defensive countermeasures system is "intelligent", with its actions directed by a central processor unit. The processor unit obtains inputs from a set of warning systems:
Not all defensive countermeasures systems will have all these elements, though an RWR is essentially a common denominator. A laser warning system is generally only seen on low-level battlefield aircraft, such as helicopter gunships, since laser guidance is not used for long-range SAMs capable of hitting aircraft at altitude. However, the latest missile warning systems may also incorporate laser warning capabilities.
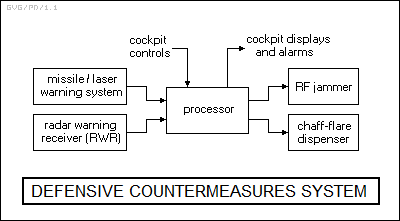
In any case, the defensive countermeasures system will alert the aircrew, generally providing an audio alarm and also some sort of threat display to identify the nature and bearing of the threat. A threat display system may be a separate display in an older aircraft, or one that has been fitted after the fact along with a defensive countermeasures system -- but in a modern combat fighter, the threats are integrated in a single display that combines radar and other inputs to give the aircrew a unified "picture" of the combat environment through "sensor fusion".
* As mentioned above, different types of RWRs may have very different capabilities. The essence of an RWR is a receiver to pick up radar transmissions. Early RWRs simply gave an alarm, and were only designed to pick up a specific radar or a small set of specific radars. If a new radar was introduced that operated on a different band, they were blind to it. Modern RWRs are based on wideband receivers backed up by a digital processor. The processor has a "library" of signatures of specific radars, and such an RWR will not only give an alarm but will identify the type of radar. It may also be able to indicate that a radar not in its library has illuminated the aircraft, but will not be able to specify the type.
RWRs may also be able to give the direction of the threat. One way to do this is to mount receiver antennas on nose, tail, and the wingtips. The RWR will compare amplitudes or time of arrival of a specific signal arriving at the four antennas to give the angle to the radar. Another approach is to use phase comparison of the signal to give the angle.
Confusingly, there are a number of different acronyms for a system that identifies and locates radars, and to make matters worse the use of this terminology has evolved over time and may differ from source to source. In general, the acronyms tend to more identify different missions instead of different technology. These acronyms include:
* The defensive countermeasures system will also automatically respond to deal with the threat. There are three classes of threats:
* One of the first lines of defense against missiles is to dispense "expendables", meaning chaff packets and flares, from a chaff-flare dispenser. The latest dispensers can cut chaff, in the form of metalized glass fibers, to the appropriate length for a particular threat radar, with the defensive countermeasures automatically programming the proper length and dumping the chaff. Modern pulse Doppler radars tend to cut through chaff fairly easily, because the chaff quickly slows down relative to the launch aircraft. One refinement is to use chaff to reflect active jamming transmissions; with the use of "jammed chaff" or "jaff", a missile will not merely be confused by the chaff, it will actually home in on it.
As mentioned earlier, active jamming can be either "disruptive" or "deceptive" in nature. Disruptive jamming can be subdivided into "broadband" or "barrage" jamming, in which noise is tossed out over an entire range of frequencies; and "spot" jamming, in which the noise is tossed out on the precise band an adversary radar is transmitting on.
The nice thing about a broadband jammer is that it can interfere with any radar operating over its band. The bad thing is that it spreads its power over the entire band, meaning it only generates a fraction of that power against any specific radar. An analogy to radar jamming is the idea of generating sound noise to drown out someone trying to talk. If the person can shout loud enough to be heard over the noise, the jamming doesn't work. Similarly, if a radar produces more powerful than the noise generated by a jammer, the radar will still work, though the noise is a nuisance. This is called "jamming burn-through".
A spot jammer can focus all its power on a particular band, making burn-through more difficult. It has problems if a radar can jump from band to band, or if multiple radars operating on different bands are present. If several aircraft are in an attacking formation, they can carry spot jammers operating on different threat bands.
The processor unit in a modern defensive countermeasures system will monitor adversary radar operation using its RWR, switching spot jamming frequencies accordingly and breaking radar lock. This technique, known as "sweep jamming", can be effective against multiple radars as well, at least up to a point, with the defensive countermeasures system breaking the lock of one radar, jumping to another band to break the lock of another, and so on. Other tricks to make noise jamming more effective is to match noise bursts to the sweep rate of a rotating radar, or reply to radar pulses with noise bursts.
One problem with noise jamming in general is that missiles can be designed with a "home on jam (HOJ)" capability, zeroing in on the jammer module from its strong emissions. A formation of aircraft, each carrying a noise jammer, can present a diffuse target, complicating life for the HOJ seeker; two aircraft can also alternate activation of their jammers, a scheme known "blinking" that confuses the missile HOJ seeker. HOJ doesn't work so well with a deception jammer, since the missile may not be able to figure out where the target really is.
BACK_TO_TOP* Since disruptive jamming tends to require large amounts of power, deception jamming tends to be more useful for defensive countermeasures systems. There are many deceptive jamming schemes and some are very ingenious.
The simple pulse repeater deception jammer has been mentioned. There are variations on the theme, such as "terrain bounce". As can be seen from watching a sunset on a beach, the flat surface of water reflects light well, and damp soil can similarly reflect radio waves. A terrain bounce jammer is a pulse repeater carried by low-flying aircraft that bounces the repeated pulses back at the ground at an angle, in hopes of persuading a missile to fly into the ground.
Terrain bounce is a form of "angle deception". Another form of angle deception is "sidelobe jamming", mentioned briefly in an earlier chapter. The idea is to pick up the transmission from a radar sidelobe, well off the boresight of the radar, and then ram a large return back down the sidelobe. The radar interprets the return as being on the mainlobe and so fails to lock onto the jammer source. Sidelobe jamming can be countered by adding a simple omnidirectional receiver antenna to the radar system; if the omnidirectional antenna detects a "true" return signal that is much more powerful than the one that the radar appears to be picking up, that's a big hint that sidelobe jamming is in progress. Of course, minimizing sidelobes also helps defeat sidelobe jamming.
Yet another angle deception scheme is known as "crosseye jamming". This involves fitting transmitter-receiver modules to each wingtip of an aircraft. In a typical scenario, the module on the left wingtip will receive a radar signal, shift it forward in phase, and pass it on to the module on the right wingtip to be transmitted back to the radar. At the same time, the module on the right wingtip will receive the same radar signal, shift it back in phase, and pass it on to the module in the left wingtip to be transmitted back to the radar. The phase-shifted signals will add up at the radar receiver to make the signal appear as if it came from some other direction -- it's much the same principle as used in a phased-array radar for electronic beam steering, except that the phase manipulation is being performed by the target. The crosseye jammer can slowly adjust the phase of the two return signals to "walk" the radar tracking off the aircraft.
* "Inverse gain jamming" or "inverse amplitude jamming" is an angle-deception technique used to disrupt tracking radars that use a sweeping procedure, such as the old nodding height-finder radars and conical scan radars. An RWR system will detect such radars from their cyclic fluctuation in intensity, and then will activate the inverse-gain jammer in response. The inverse gain jammer feeds back an enhanced return during the low-intensity part of the scan cycle and little or no additional return during the high-intensity part of the scan cycle. This fools the radar into either judging it has a lock on target when it doesn't, or doesn't have a lock on target when it does.
There are counter-countermeasures against inverse gain jamming. One is to use two antennas, one for transmit and one for receive, and only rotate the receive antenna to perform conical scan -- eliminating the telltale cyclic fluctuation of the transmit signal. This scheme is known as "conical scan on receive only (CSORO)" or more generally "Lobe On Receive Only (LORO)". An inverse gain jammer can deal with this countermeasure to an extent by blindly generating its inverse-gain cycle and testing it to see if it forces the radar to break lock.
* There are also "range deception" techniques. The simple pulse repeater is an example of a range deception scheme, but there is a more sophisticated variation on the same theme, known as "range-gate pull-off (RGPO)". When an aircraft is illuminated by a range-tracking radar, the RGPO jammer initially acts like a radar transponder, picking up the radar pulse, amplifying it, and sending back immediately. This actually increases the magnitude of the return, which would seem counterproductive. However, the jammer is simply "setting up" the radar for a fall, using the strong echo to force the radar receiver's automatic gain control to reduce gain.
The RGPO jammer then emits a delayed pulse along with the instantaneous pulse, gradually increasing the power of the delayed pulse while pulling down the power of the instantaneous pulse down to zero. When this occurs, the radar remains locked on the delayed pulse, which is still powerful enough to ensure that the receiver's AGC remains set to a low level. Under such conditions, the radar will not notice the actual echo from the aircraft and, because of the strong delayed pulse, will not be able to correctly estimate the distance to the aircraft.
The jammer will then increase the pulse delay, making the aircraft seem even farther out of range. The jammer then switches off, leaving the radar with a broken target lock. If the radar tries to lock onto the aircraft again, the range deception jammer plays the same game once more. Radars can defeat this range deception game by varying PRF or pulse band, forcing the jammer to start over. Radars can also monitor the magnitude of the return, checking to see if the return seems to brighten excessively; if so, the radar can then track on the "leading edge" of the return, focusing on the actual return and ignoring the delayed pulse.
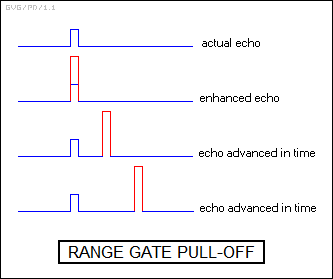
There is a similar "velocity gate pull-off" scheme that works much the same way, except that the frequency of the deception signal is adjusted instead of the time delay to give a false Doppler frequency for the target.
* One of the relatively recent innovations in defensive countermeasures is the "towed decoy". A towed decoy is a pulse repeater, containing a miniature TWT to echo radar signals tracking the aircraft, causing a radar-guided missile to home on the decoy. Signals and power are provided over the towline, and the assembly is cut loose with a "guillotine" assembly before landing.
The first to be used in action was the Raytheon "AN/ALE-50", which was towed behind B-1B bombers and F-16 fighters during the NATO Kosovo campaign in the Balkans in 1999. It worked so well that crews called it the "Little Buddy". It has been followed by the "AN/ALE-55" towed decoy, which uses a fiber-optic cable instead of an electrical cable. Other nations have now introduced towed decoys into service. Some pilots were dubious of towed decoys at first, but modern radar-guided AAMs and SAMs are hard to trick, and they can pull up to 40 gees in turns, making them impossible to outmaneuver.
Another interesting concept in modern deceptive countermeasures is to build a jammer system that actually sends an antiphase copy of the radar signal back at a radar receiver, with the antiphase signal mostly or completely eliminating the return echo, rendering the jammer platform invisible to radar. This is very tricky to do, and it is unclear if any contemporary jammer systems can do it -- but it may be a feature of some modern jammers whose details remain classified.
BACK_TO_TOP* Offensive countermeasures systems tend to be more "brute force" than defensive countermeasures systems. Offensive jamming is generally based on high-power disruptive jamming schemes. The idea behind deception jamming is to make a platform seem to be something or somewhere it's not; in offensive jamming, concealing the jamming platform is not the objective, it's ensuring that other platforms can't be seen on radar. A dedicated jamming platform can commit large amounts of power to its disruptive jamming systems, giving them greater effectiveness.
Of course, disruptive jamming can also be used against communications signals, and in fact communications jamming well predates radar jamming. It is somewhat more difficult than radar jamming; jamming a radar means dealing with a relatively faint return trace, while jamming a communications channels means dealing with a strong direct transmitter channel. One trick is to feed back a voice conversation after a delay, resulting in an incoherent garble. Comparable disruptive signals can be fed back into a digital communications channel. In some cases, communications jamming is used in complement with radar jamming, in attempts to block channels used by ground controllers to communicate with interceptor aircraft.
If a jamming aircraft actually accompanies aircraft on strikes over defended airspace, it is a "penetration jammer". If it remains outside of defended airspace, it is a "standoff jammer".
The best-known Western offensive jamming aircraft at the present time is the Boeing "EA-18G Growler" ECM derivative of the Super Hornet fighter. It is a two-seat aircraft, with the pilot in the front seat and the ECM operator in the back seat. It is fitted with AN/ALQ-218 wideband receivers to spot threats, and can carry up to five AN/ALQ-99 jamming pods, each powered by a turbine spinner on the nose. The Growler also features an INCANS communications jamming system, and datalinks to share threat data with other platforms. The AN/ALQ-99 pod is obsolescent, and is now being replaced by the "Next Generation Jammer" pod -- featuring an AESA, and produced in low-band and mid-band variants.
* There is a more drastic approach to dealing with enemy radars: destroy them, a scheme referred to as "Suppression of Enemy Air Defenses (SEAD)". The US found this an urgent need during the Vietnam War, leading to the development of two pieces of technology: a RHAWS, to detect, classify, and target radars, and an "antiradar missile (ARM)" to home in on the radar and destroy it. Incidentally, the general term "antiradiation" is sometimes used instead of "antiradar", since an ARM may have a seeker that allows it to take on other emitters, such as communications centers or navigation beacons. In any case, a series of "Wild Weasel" aircraft were fitted with a RHAWS and with ARMs to have it out with enemy radar sites. Once the radar was destroyed, the "blinded" air-defense site could be pounded with bombs.
The first US ARM to go into widespread operational service was the "AGM-45 Shrike", which was a Sparrow AAM with a radar seeking head. It was replaced by the current Western standard ARM, the "AGM-88 High-Speed Antiradiation Missile (HARM)", which is something like a scaled-up Shrike, with much improved systems. Shrikes had to be fitted with a different anti-radar seeker head before a mission, depending on what kind of radar they were intended to engage. A HARM is bigger, faster, and carries a single seeker that can home in on a wide range of radars. A Growler typically carries two HARMs along with its jamming gear.
HARM has been continually refined during the course of its service. HARM is likely to be eventually replaced by a "multimode" missile that can be used as an AAM, an ARM, or even a ground-attack missile, allowing an aircraft to carry a single class of missile to deal with different classes of threats and targets.
BACK_TO_TOP* Along with jamming, spoofing, or destroying enemy radars, there is another option for neutralizing them: "stealth", or making the target impossible to pick up on radar.
The RCS of an aircraft or other platform is dependent on a number of factors, including size; the materials it is made from, with metals providing a high RCS and composite graphite-epoxy a lower RCS; and the shape, with sharp boxed-in corners acting like corner reflectors and increasing the RCS. Work on "low-observable" aircraft with a minimal RCS goes back to the 1960s.
In the early 1960s, the Air Force obtained a series of high-altitude reconnaissance variants of the Ryan Firebee target drone. The Firebee was small, meaning it had a low RCS to begin with, and modifications were made to reduce its RCS further. One modification was to put a mesh screen over the engine intake. The moving compressor blades of a jet engine tend to be very "bright" on radar, sort of like a spinning disco ball flashing in a spotlight, a phenomenon known as "glint"; the screen kept the radar pulses from entering the inlet. Blankets of "radar absorbing material (RAM)" were also applied to the sides of the Firebee to soak up radar pulses.
In the 1970s, the US developed the first operational aircraft designed from the ground up for "stealth", the Lockheed F-117 Nighthawk. This aircraft had a "faceted" design, with an airframe composed of flat planes that reflected radar pulses in angles away from the transmitter beams, and was heavily coated with RAM. Doors had "zigzag" edges to break up radar returns. The engine inlets had a "serpentine" design to prevent the engines from being visible to radar.
The F-117 also had wide, flat engine exhausts that reduced the aircraft's infrared signature. It did not carry a radar since its emissions might announce the aircraft's presence, instead using an inertial navigation system for guidance and an infrared video camera for targeting. Radars can be made more compatible with stealth by designing them for LPI operation. Unfortunately, having a radar tends to reduce stealth even if the radar isn't working. This is because the radar has a reflecting dish or a radar array that is only concealed by a radome that is necessarily transparent to radar, and that dish makes a nice radar target for hostile radars. However, with AESA it's possible to make antennas with configurations that are poor radar reflectors.
The F-117 was followed by the much larger Northrop Grumman B-2 Stealth bomber. This aircraft uses most of the same stealth principles, but the implementation is different in many ways. For example, instead of having a faceted airframe like the F-117, the B-2 features smooth curves. Incidentally, a stealthy aircraft is optimized for stealth from the forward bottom viewpoint, which is what a hostile radar would be tracking as the aircraft came up on the target. It is difficult to make an aircraft stealthy from all aspects.
The F-117 has been retired, having been replaced by the more capable Lockheed Martin F-35 Joint Strike Fighter; while the B-2 is to be replaced by the superficially similar but much more sophisticated Northrop Grumman B-21 Raider. Many modern combat aircraft that weren't designed to be highly stealthy like the F-117 or B-2 still have some stealth features -- not to make them invisible, but to reduce their RCS, and so make their countermeasures systems more effective.
Interestingly, low-frequency radars are better at picking up stealth machines than high-frequency radars -- though they don't have the resolution to permit them to be targeted. In addition, if a radar operating on a high-altitude platform scans a stealth aircraft flying at low altitude, it will be able to spot it as an uncluttered "hole" in the radar returns from the ground clutter.
BACK_TO_TOP