
* While US codebreakers were working against Japanese codes and ciphers, the British, leveraging techniques developed by Polish codebreakers, made their own remarkable penetrations of German ciphers at the British codebreaking establishment at Bletchley Park. This chapter and the next outlines the accomplishments of British codebreakers during World War II.
* The British Room 40 cipher bureau continued to crack German ciphers after the First World War, or at least they did until 1926. Then they began to receive messages that were absolutely opaque.
The German military had put Arthur Scherbius's Enigma cipher machine into use. The British, the French, and the Americans all tried to crack Enigma, and they all failed, partly because they did not try very hard. Germany was at the time generally disarmed, in disarray, and not much of a threat, and after the terrible bloodletting of the Great War nobody thought anyone would be crazy enough to want to start a serious war any time soon. There was no pressure to crack a difficult cipher as Enigma.
The Poles were not so complacent. Poland was now independent after a long period of division between Russia and Germany. The Poles wanted to remain independent, while both the Germans and the Russians wanted to regain their lost Polish territories. The Poles established the "Biuro Szyfrow (Cipher Bureau)", to provide intelligence on their enemies. The Biuro Szyfrow proved its worth in the Russo-Polish War in 1919:1920, when it provided valuable intelligence that helped defeat the Soviet invasion of Poland.
When the Biuro Szyfrow encountered Enigma in 1926, Polish codebreakers were just as baffled as everyone else. A Captain Maksimilian Ciezki was in charge of deciphering German messages. He knew about the Enigma machine and in fact had access to a commercial version of it, but that did him only a small amount of good. The rotors of the military version were wired differently, and even if the rotor wiring was known, there was still the difficult problem of determining the daykey that defined the daily Enigma configuration. Ciezki made no progress on Enigma until 1931, when simple luck handed him the solution to a good part of the problem.
* Hans-Thilo Schmidt was then a 43-year-old employee of the German "Chiffrierstelle", which administered German enciphered communications. He was also embittered from a number of reverses of fortune and in need of money -- an unfortunate combination for someone in a sensitive position. In 1931, Schmidt contacted French intelligence and arranged a very profitable sale of information about the Enigma.
The documents provided the rules for using an Enigma machine and gave hints that could help determine the rotor scramblings, though they did not define the wiring between the keyboard and the first rotor. Schmidt's documents were a major step towards overcoming the first obstacle for deciphering Enigma messages, but the French did little with the intelligence themselves. However, the French had an agreement with the Poles for sharing such intelligence, and passed the documents provided by Schmidt on to the Biuro Szyfrow. Captain Ciezki now had half of a grip on Enigma.
The Biuro had recruited a number of mathematicians from the university at Poznan to help them crack Enigma. Poznan had been part of Germany before the reconstruction of Poland, and these mathematicians were all fluent in German. Recruiting mathematicians was an innovative step on the part of the Poles. Traditionally, linguists had been regarded as the best candidates for codebreakers, but now the field had become more technical, and a technical mind was regarded as possibly better suited to the job.
The star among this group was a quiet 23-year-old named Marian Rejewski. He had been studying statistics and intended to work in the insurance industry. Had he done so, he would likely never have made much of a mark on the world. Instead, he earned himself a place in the history books, of cryptology at least, and helped change the course of the coming war.
Rejewski was assigned to work on Enigma. The first problem was to determine the wiring arrangement of the Enigma machine. Rejewski figured out the wiring of the rotors using some mathematical logic and clues provided by Schmidt, and then the wiring between the keyboard and the first rotor of the military Enigma machine. He thought the matter over for some time, and then made an assumption: what if the Germans hadn't bothered to scramble the wiring at all? That it was in straight ABCD order? That turned out to be the case. Sometimes the obvious and stupid answer is the right one.
* Over their first obstacle, the Poles ordered the construction of an Enigma machine that worked in exactly the same way that German military Enigma machines did. However, the second obstacle remained intimidating. Rejewski had to figure out some way of determining the daykey, the combination of rotor order, rotor position, and plugboard settings that German Enigma operators all set their machines to every day.
There were procedures that the Germans could use in Enigma operation to further complicate the lives of would-be codebreakers. One possible procedure was to have the first three characters in a message define new rotor settings that would be used for the rest of the message. These three characters would be chosen, in principle, at random by the Enigma operator. They were referred to as the "message key". The message key would be sent using the default daykey setup, but once sent, the sending operator would then change the rotor positions to the random characters he or she had selected. The Enigma operator on the receiving end would read the message key using the default daykey setup, and then adjust the rotors on his or her Enigma machine as well.
This scheme would ensure that of all the different messages sent by Enigma operators during one day, only the message keys of all the messages would be enciphered using the same daykey setup. The rest of each message would be enciphered using the new rotor positions specified by the random message key selected by each Enigma operator, ensuring that each message after the message key was enciphered differently from all other messages sent that day. This reduced the sample size of text enciphered with the same key, complicating analysis by a codebreaker.
The Germans implemented this procedure, but specified that the message key be sent twice to make sure that it was correctly received. This meant that in practice the first six characters, not just the first three, of all messages sent during one day were all enciphered using the same daykey, while the following text was enciphered differently using the new rotor positions. The Germans didn't believe this procedure would compromise the security of Enigma -- but any predictable features in an encrypted message tend to weaken security, and the use of this redundancy allowed the Enigma to be cracked, at least for a while.
* What Rejewski did, in outline, was determine that the redundant message keys could be used to obtain a logical pattern, or "fingerprint", that was characteristic of the initial placement and orientation of the rotors, regardless of the plugboard settings. The Poles could then use their own Enigma machines to come up with a catalog of the fingerprints associate with the 105,456 possible initial rotor arrangements and orientations. They could then analyze all the intercepted Enigma messages for one day, determine the fingerprint of the messages, look up the corresponding fingerprint in the catalog, and obtain the rotor setup.
This didn't give them the plugboard settings. There were 100,000 million possible plugboard settings, but all they did was define a monoalphabetic substitution cipher, and anyone could crack such a cipher quickly given a moderate amount of ciphertext. In practice, the plugboard settings could be generally very quickly determined using a little clever guesswork.
* That's the general scheme -- now for the details. The path Rejewski took to find his fingerprint was far from obvious, even in hindsight. He began by considering the first six letters in all the Enigma messages intercepted in one day. They would be random-looking strings of the form:
: XHRKBN : QAZLKL : BJLOWI
-- and so on. Rejewski had no idea what plaintext message key they actually represented, since he didn't know the daykey. All he knew was that they were all enciphered using the same initial daykey setup, and that in each string the same plaintext message key was enciphered by the first three ciphertext characters and the second three ciphertext characters. That meant that the first ciphertext character in all these strings represented that same plaintext character that the fourth character did. The same was true of the second and fifth characters, and the third and sixth character.
: X--K-- : Q--L-- : B--O--
For all such strings collected from a day's messages, the first character was the result of encipherment with all the Enigma machines in the same "state", configured to the same initial setup and with the rotors in the starting position. Similarly, the fourth character in all the strings was obtained from all the Enigma machines in the same state, with the same initial setup, but with the rotors moved forward by three positions.
Rejewski tabulated the relationships between the first and fourth characters as follows, using the example set above:
: ABCDEFGHIJKLMNOPQRSTUVWXYZ : O L K
Given enough messages intercepted in one day, he could complete this table, giving him something like:
: ABCDEFGHIJKLMNOPQRSTUVWXYZ : FOXPVBUNWYACRIZELDTQGJMKHS
This seems to be leading nowhere, but Rejewski kept playing at it and discovered a higher-level order in these relationships.
He noticed that "A" in the top row was related to "F" in the bottom. He went to "F" in the top row and saw that it was related to "B" in the bottom. He went to "B" in the top row and saw that it was related to "O" in the bottom. He continued this search until he ended up with the "A" in the top row again, and then repeated this game through the rest of the table until there were no more characters left. The example above gives:
: A -> F -> B -> O -> Z -> S -> T -> : Q -> L -> C -> X -> K -> A : D -> P -> E -> V -> J -> Y -> H -> N -> I -> W -> M -> R -> D : G -> U -> G
-- or three "chains" of characters. Two of the chains have 12 links in the chain, and one chain has two links in the chain.
Rejewski kept on playing this game with different sets of messages sent on different days, and noticed that the pattern of the number of chains and the number of links in the chains varied widely from day to day. In a brilliant leap of intuition, he realized that this pattern provided a fingerprint characteristic of the initial rotor setup. Each initial rotor setup had a different fingerprint, or at worst the number that had the same fingerprint was small, allowing the proper rotor setup to be determined with a little trial and error.
The important thing about this fingerprint is that it depended only on the number of chains and on the number of links in the chains; the exact characters in the chains were irrelevant. Given the same initial rotor setup, changing the plugboard would change the characters, but it wouldn't change the pattern. The only important data was the pattern, which in the case above came down to:
: * -> * -> * -> * -> * -> * -> * -> * -> * -> * -> * -> * -> * : * -> * -> * -> * -> * -> * -> * -> * -> * -> * -> * -> * -> * : * -> * -> *
-- or two chains of 12 characters, and one chain of 2 characters. The Poles then could take their own Enigma machines and catalog all the 105,456 possible rotor positions and their fingerprints, with the catalog having entries something like:
: 1 chain with 10 characters : 2 chains with 5 characters : 1 chain with 6 characters / rotor order ACB rotor position XHJ : : 1 chain with 13 characters : 1 chain with 5 characters : 2 chains with 4 characters / rotor order BAC rotor position FCD
-- and so on. It was a lot of work, but it could be and was done. Once the catalog was finished, the Poles could then identify the fingerprint for Enigma messages intercepted during one day, cross-reference it in their catalog, and know what the rotor setup was.
* That still left the plugboard setup as an unknown, but as noted all that amounted to once the rotor setup was determined was a monoalphabetic substitution cipher. Frequency analysis could be used to crack it, but since only 12 characters were swapped, a clever codebreaker could puzzle it out with little trouble. For example, given partly decrypted text at the front of a message of the form:
: LIEHLETHIR
-- the codebreaker might have a hunch that it meant "Heil Hitler". The implication was that "L" and "H", and "E" and "I", were swapped. A little toying with the plugboard setups was often enough to unravel the message. The more than 100,000 million possible plugboard setups turned out to be the least of the obstacles the Poles had to face.
* Figuring out how to crack Enigma took an enormous amount of effort on Rejewski's part, but by 1934, the Poles were reading Enigma messages on a regular basis. Every time the Germans changed their cipher procedures, the Poles had to rebuild the catalog of fingerprints, but by that time Rejewski had figured out a way of replacing the catalog with a machine similar to an Enigma that could search for the rotor orientations corresponding to a particular fingerprint. The machine was called a "bomba", for reasons that remain somewhat obscure. It may have been because the machine ticked like a bomb, or because Rejewski was eating an ice-cream confection named a "bomba" when he thought of the idea.
A bomba checked all the 17,576 positions of three rotors, but since there were six different possible arrangements of rotors, the Poles had to build six "bomby" (plural of bombs). The six bomby were stored in a rack about a meter high, and could crack a daykey in about two hours. The irony of all this work was that the Poles actually had the daykeys anyway. Hans-Thilo Schmidt had continued his work with French intelligence, meeting with his French contact twenty more times into 1938. He sold the French the codebooks listing daykeys, and the French handed the codebooks over to the Poles. However, the head of the Biuro Szyfrow, Major Gwido Langer, knew that the Poles could not rely on obtaining such intelligence, and didn't tell Rejewski or his colleagues about the codebooks to make sure that his people came up with their own reliable way to crack Enigma. Langer kept the codebooks locked up as a backup in case of emergency, but they were otherwise left unused.
* The Poles' success with Enigma came to an abrupt end in 1938 when the Germans improved their communications security by providing Enigma operators with two more rotors. An Enigma operator could now arrange three rotors in:
: 5 * 4 * 3 = 60
-- different ways, not just 6. This meant that the Poles had to build ten times as many bomby, and there just wasn't the money to do it. Worse, Hans-Thilo Schmidt had finally decided to stop passing on information and the French were no longer receiving Enigma codebooks. Incidentally, the Germans also increased the number of plugboard cables from 6 to 10, allowing 20 characters to be swapped instead of 12. This increased the number of plugboard settings to:
: 26! 20! : -------- * --------- = ~151,000,000,000,000 : 6! * 20! 10! * 2^6
However, if this measure had been taken without adding two new scramblers, it wouldn't have inconvenienced the Poles much. They would have had to guess a little harder to figure out the cable settings, or resort to frequency analysis.
In late April 1939, Germany repudiated its non-aggression pact with Poland. Given Hitler's increasingly poisonous rhetoric against Poland, few could doubt that Fuehrer intended to invade the country soon. On 30 June 1939, Langer wired his French and British counterparts, asking them to come to Warsaw to discuss matters of mutual importance. Langer gave few details, but puzzled representatives of the two friendly nations' cipher bureaus showed up on 24 July anyway.
Langer told them that Poland had cracked the Enigma, and showed them the bomby. The visitors were astounded, since they believed Enigma could not be cracked. Dilly Knox of the old Room 40 crew was there, and asked Rejewski how they'd figured out the key mapping to the rotors, and Rejewski simply replied that he'd guessed correctly that it was in alphabetical order. Knox replied: "Oh, God, we never thought of that! It's too obvious! Why didn't we think of that?!"
The Poles handed over two German military Enigma replicas to the French and British, as well as plans for a bomba. A little over a month later, on 1 September 1939, Hitler invaded Poland. The Poles were crushed within weeks by overwhelmingly superior German forces. Rejewski fled to France, and after the German invasion of France in the spring of 1940 made his way to Britain, where he did menial cipher work for British intelligence. For some reason, probably simple bureaucratic ignorance, nobody recognized the true value of his skills.
BACK_TO_TOP* By that time, the British were working on breaking Nazi codes in earnest, and the information passed on by the Poles would prove very important. The British were fighting Hitler from an underdog position, and put a high priority on intelligence gathering to help even the odds, building up their codebreaking operation as fast as possible.
There was no space for all the freshman codebreakers at Room 40, so in 1938 they had been sent to the new "Government Code & Cipher School (GC&CS)" at the estate of Bletchley Park in Buckinghamshire, 80 kilometers (50 miles) north of London, where a very large staff could be accommodated.
There was a large manor at the center of the estate that housed the headquarters, but in time most of the staff work was conducted in hastily built wooden buildings, or "huts". Each hut contained a different group of specialists. As the staffing grew, each "hut" grew into a collection of buildings, and eventually terms such as "Hut 3" meant a sub-organization instead of a specific building. Data obtained from the decrypts was filed away in a card-file system housed in the C-block building, and the filtered decrypts were passed up to a central organization called the "hut watch" for final translation and distribution to military teams for evaluation.
Bletchley Park was assigned the codename "Station X". The cryptanalysts became fond of the place, redefining the organization's acronym as standing for the "Golf, Chess, & Cheese Society", reflecting common interests among their ranks. There were 200 people at Bletchley Park in the beginning, including some of the Room 40 old-timers like Dilly Knox and Nigel de Grey, but the staff would increase to thousands in a short time.
Like the Poles, the British had recognized the value of recruiting mathematicians and scientists. The Room 40 group had focused on linguists as had long been tradition in codebreaking, but now the codebreakers there began to search through their networks of contacts to find new recruits from mathematics departments at universities such as Cambridge, Oxford, and Newnham College.
One of their more unusual catches was a rumpled, unshaven, eccentric Cambridge mathematician named Alan Turing. Turing had already demonstrated that he was a genius in 1936 by describing in a mathematical paper an imaginary device he called a "universal machine" and was later named a "Turing machine", which was one of the conceptual steps towards the development of the modern computer. Turing would prove a vital and prominent asset to the British codebreaking operation.
* The British were cracking Enigma traffic from early on. They had more resources than the Poles and were able to build the 60 "bombes" (as the British referred to them) now needed to decipher Enigma messages, using the same techniques that Rejewski and his colleagues had pioneered. The Germans had learned nothing after their invasion of Poland about the success of the Poles in cracking Enigma, and Bletchley Park was pouring out valuable intelligence by the first months of 1940. The Enigma decrypts proved particularly important in that Battle of Britain in the summer of 1940, providing the British Royal Air Force with valuable clues on the strength and organization of attacking Luftwaffe forces, as well as intended targets.
Bletchley Park not only cracked Enigma messages, the codebreakers there also worked against Italian codes. The intelligence provided by Bletchley Park was codenamed "ULTRA", which was short for "ULTRA SECRET". British Prime Minister Winston Churchill appreciated the value of ULTRA intelligence, and took a strong personal interest in the workings of Bletchley Park. He took a tour there on 6 September 1941, and after meeting the mixed lot of scholars and eccentrics, commented to Sir Steward Menzies, head of the British Secret Intelligence Service (SIS, no relation to the American SIS): "I told you to leave no stone unturned, but I didn't expect you to take me so literally."
That implied no disrespect to the ULTRA personnel, which he called "the geese that laid the golden eggs, and never cackled." When Turing and a few of his colleagues, frustrated by a lack of resources, took the insubordinate step of going over the heads of their own superiors and writing a letter to Churchill directly, he responded by immediately ordering that the Bletchley Park work be given the highest priority.
BACK_TO_TOP* The British developed refinements of the techniques they had inherited from the Poles. For example, they figured out that sometimes Enigma operators used predictable message keys, such as consecutive keys on the keyboard, or initials of a girlfriend, and so on. These predictable message keys were called "cillies", a term picked up from the Poles because they had noticed one German Enigma operator had a girlfriend with the initials CIL. By a similar logic, cillies were also called "femmes". Exactly what importance this discovery had is a little puzzling, since the scheme inherited from the Poles was focused on finding the daykey, not the message key. It probably provided some help in determining the plugboard settings.
The British also discovered that the Germans had come up with procedures intended to make daykeys harder to crack, with exactly the opposite results. For example, there was a rule that a scrambler couldn't stay in the same position two days in a row. Without this rule, there were 60 possible scrambler settings. However, this dropped 28 of the possible scrambler settings, cutting the work almost in half. Similarly, there was a rule that two characters next to each other in the plugboard could not be swapped. This simplified the guesswork needed to unravel the plugboard settings. Anyone who has ever played the ROCK-PAPER-SCISSORS game knows that doing the same thing twice in a row is a useful tactic for fooling an opponent, but apparently the Germans forgot that trick.
* Rejewski's approach to cracking Enigma messages exploited the fact that the Germans blundering by sending the message key twice. They couldn't be guaranteed to blunder indefinitely, and so Bletchley Park needed a backup plan for the day the Germans wised up. Turing was given the job, and managed to come up with a new approach that did not rely on the duplicated message key.
Turing's scheme was similar to Rejewski's approach in that he found a "fingerprint" that was characteristic of the rotor setup and independent of the plugboard setup. However, instead of deriving the pattern from the encipherments of a duplicated message key, he derived the pattern from the encipherment of a crib, such as:
: heilhitler
As noted, military communications tend to be fairly rich in cribs; military weather reports, for example, will generally be in a standard form and have predictable fields. Anyway, given the crib above, it might be enciphered as:
: TVLKPHIELJ
Turing started playing games with the relationship between the presumed crib and its ciphertext, much as Rejewski had played games with the enciphered message keys, to see if patterns emerged, but Turing's game only involved a crib in one message and the ciphertext it generated -- not a list of relationships derived from many messages.
Turing noticed that he could sometimes establish a logical "loop" between a crib and its ciphertext. In the example above, the first character in the plaintext string is "h", and it is encrypted as a "T". Turing then found the "t" in the plaintext string, and obtained its ciphertext character as "I". There are two examples of "i" in the plaintext string, with the first "i" being enciphered as "L" and the second being enciphered as "H". This chain of relationships started out with an "h", so the second "i" closes the loop, which is what we want. Following the possible links from the first "i", in contrast, goes to several dead ends that do not close the loop, and so this first "i" is not useful.
Turing's game has yielded a loop of characters between crib and ciphertext:
Now let's suppose Turing had three Enigma machines, modified so that instead of having a keyboard and light bank up front, they had a set of electrical sockets going in and a set of sockets going out, with the sockets in each set corresponding to the characters in the alphabet. Turing could use his three modified Enigma machines to hunt for possible rotor positions of the actual Enigma machine being targeted.
Assume for the moment that the Enigma machine didn't have a plugboard, and that the rotor selection and placement for the target Enigma machine is known. Given these assumptions, then the problem was to determine the rotor orientations. Turing could hunt for the proper rotor orientations as with the following procedure:
The Enigma machine was an electromechanical device, and encipherment between a plaintext key and a ciphertext light was established with an electrical connection through the plugboard and the rotors. This means that with the three modified Enigma machines cabled together like this, when the rotors finally hit the orientations matching that in the target Enigma machine at the beginning of the crib, there would be a complete electrical connection from "T" to "t" to "I" to "i" to "H" to "h", with the light turning on. The rotor setup would be known.
Of course, there might be more than one rotor orientation that turned the light on, but this scheme was certain to greatly reduce the number of possibilities. The more complicated the loop, the less likely multiple matches would be, reducing the workload for the codebreaker, and if multiple loops were known, they could be used to screen out false matches.
* This scenario assumed that the plugboard didn't exist, but unfortunately it did. Turing realized that all the plugboard did was shuffle the characters going into the rotor bank around, and so if he cabled all 26 characters through all three modified Enigma machines and ran them through an external box with 26 lights, eventually at least one of the lights would turn on. This multiplied the likelihood for false matches, but again this still greatly narrowed down the number of candidates.
As with Rejewski's fingerprint, Turing's fingerprint did not depend on specific characters. All Turing knew was that if he identified such a loop from a crib, he could wire together a number of modified Enigma machines matching the number of characters in the loop, move the rotor orientation ahead in each machine to its position in the loop, and then set the rotors in the three machines moving forward in step automatically until a light turned on. The fingerprint only depended on the number of characters and their relative order in the loop.
We also assumed that the rotor selection and placement was known, and that wasn't a valid assumption, either. The only way to deal with this issue was exactly as the Poles had: try them all in parallel. Turing's approach meant a large number of modified Enigma machines, since there were 60 possible rotor arrangements, and searching with a loop that had, say, five characters in it meant using five machines with the same rotor arrangement, then 300 modified Enigma machines would be required to do the job entirely in parallel. The parallel searches also increased the likelihood of false matches, but again, this was manageable.
* The key elements in Turing's scheme were the rotors and the connections, and Turing and his Cambridge colleague Gordon Welchman came up with plans for a streamlined system that could deal with loops up to 12 characters long. Welchman provided an important enhancement to Turing's concept in the form of the "diagonal board" -- a plugboard array to help deal with the Enigma's Stecker.
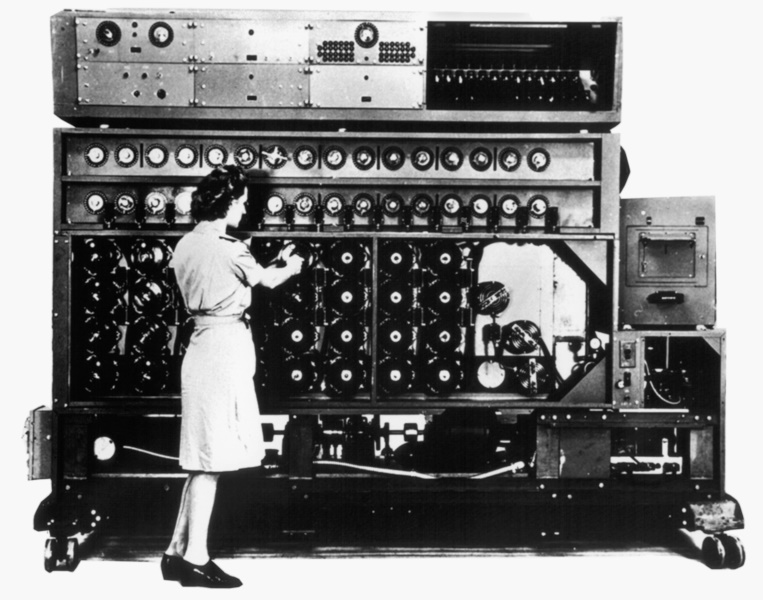
The two mathematicians passed their design on to an engineer named Harold "Doc" Keen of British Tabulating Machines (BTM). No doubt shaking his head at the odd notions mathematicians had of how to build something, he reworked the design considerably. A prototype bombe, named VICTORY, was delivered in March 1940, but it was too slow to be useful. A completely redesigned and effective bombe named "AGNES DEI" or just "AGNES" was delivered in early August.
In the meantime, as the British had feared, the Germans finally had realized that repeating the message key wasn't a good idea. They changed their procedures on 10 May 1940 and eliminated the practice. AGNES showed up just in time, with the Battle of Britain approaching a peak. Within a year and a half, Bletchley Park had sixteen bombes in operation, and BTM would ultimately build a total of 210.
A bombe was about a little less than two meters high, a little more than two meters long, about 60 centimeters deep, and weighed about a tonne. All but the earliest had 36 sets of three rotors. Connections were tested at a rate of 100 times a second, and when a match was found, the machine stopped. One of the operators, usually a WREN (a member of the Women's Royal Naval Service), would write down the "stop" value and set the bombe to running again.
With the bombe, Enigma keys could often be cracked in a few hours. It was never a cut-and-dried operation, however, and obtaining a daykey still took judgement, cleverness, skill, and a bag of tricks. For example, one particular sticking point was that Turing's approach relied on a crib. The assumed crib might not actually be in the message -- or if it was, it might not be where it was assumed to be.
BACK_TO_TOP* Just as Bletchley Park was coming up to speed on Enigma, the UK and the US were joining hands on codebreaking. With the US and the UK coming closer after the fall of France to the Nazis in the spring of 1940, Churchill had believed it in Britain's interests to share some of the advanced military technology developed in the UK with the USA. Handing the Americans the new technology would ensure that they were better prepared to fight the Axis if and when the time came, and hopefully they would reciprocate. On 8 July 1940, the British ambassador to the USA, Lord Lothian, sent a letter to President Roosevelt suggesting an exchange of information:
QUOTE:
Should you approve the exchange of information, it has been suggested by my Government that, in order to avoid any risk of the information reaching our enemy, a small secret British mission consisting of two or three Service officers and civilian scientists should be dispatched immediately to this country to enter into discussions with Army and Navy experts ...
His Majesty's Government would greatly appreciate it if the United States Government, having been given the full details of any British equipment or devices, would reciprocate by discussing certain secret information of a technical nature, which our technical experts are anxious to have, urgently.
END_QUOTE
It was exactly the sort of idea that immediately appealed to Roosevelt, and the president brushed off objections by senior advisers, including General Marshall. The wheels were put into motion for the meeting, with a team under Sir Henry Tizard, a senior scientific adviser to the British government, arriving in the USA in late August 1940 to confer with American experts. The British brought with them a treasure trove of advanced military technology, particularly radar. The "Tizard Mission" would prove extremely valuable to the Allied cause.
One secret that the Tizard Mission did not share with the Americans was ULTRA. Churchill obviously did not think the Americans had a "need to know" that was comparable to the risk of revealing the existence of ULTRA to them. However, in October 1940, Churchill found out that the US Army SIS had cracked the Japanese PURPLE cipher machine and produced PURPLE analogue machines to read it. Now collaboration on codebreaking became much more interesting.
After discussions, in November a top-secret agreement was hammered out between Britain and the US to provide for "a full exchange of cryptographic systems, cryptanalytical techniques, direction finding, radio interception, and other technical communication matters pertaining to the diplomatic, military, naval, and air services of Germany, Japan, and Italy."
The Americans assembled a delegation to be sent to the UK for discussion. Friedman was originally pegged as the main US Army representative, but due to health problems he was replaced by Sinkov, who had been given the rank of captain. Sinkov was accompanied by Army Captain Leo Rosen. The Navy delegation consisted of two officers of OP-20-G, Lieutenant Robert Weeks and Lieutenant JG Prescott Currier. The team departed for the UK on the battleship HMS KING GEORGE V from Annapolis, Maryland, on 24 January 1941; they carried "gifts" for their British counterparts, most significantly the first PURPLE analogue sent to the UK.
The delegation arrived at the Royal Navy base at Scapa Flow in the Orkneys two weeks later, transferring to a cruiser to complete the journey. After some excitement when German aircraft attacked the convoy, the team arrived in Britain and were driven to Bletchley Park. They had wide access to the Bletchley operation; while some authors have claimed the British withheld information about cracking Enigma from the Americans, in fact Churchill personally authorized that they be briefed on the matter.
The notion that the British had kept them in the dark on Enigma appears to have arisen from the fact that the visitors were sworn to secrecy and didn't mention it in their written reports. The only administrative difficulty the visitors had was when the US naval attache at the American embassy in London tried to get the two Navy men to tell him what they were doing in the UK. They flatly refused to tell him, and he threatened to have them court-martialed -- though no doubt he would have been a sad person if he had tried. After the meetings, the delegation sailed back to Nova Scotia, from where they were brought home on a US Navy destroyer. They didn't take an Enigma machine with them; the Americans wouldn't be up to speed on Enigma until well into 1942.
BACK_TO_TOP* One of the other things that made life difficult for the Bletchley Park codebreakers was that the Germans operated several different Enigma networks. The Luftwaffe had its own Enigma network with its own books of daykeys, the German Army in North Africa had its own Enigma network, the German Navy had its network, and so on. Determining the daykey for one network did little to help find the daykey for another.
Procedures also differed between the German networks. The Luftwaffe network was the most lax, while the German Navy network was the most disciplined. The German Navy Enigma operators could select from eight rotors, meaning there were (8*7*6 = 336) possible rotor permutations, and they could adjust the position of the reflector, multiplying the possible configurations by another factor of 26. Furthermore, German Navy Enigma operators were trained to high standards, and were careful to avoid cribs when they could.
In the spring of 1941, the Battle of Britain ended as Hitler reassigned the Luftwaffe the mission of supporting the Nazi attack on the Soviet Union. However, at the same time the German Navy U-boat submarine blockade on Britain began to become increasingly effective and deadly.
The head of the German Navy's U-boat force, Admiral Karl Doenitz, had developed "wolfpack" tactics in which U-boats ganged up on convoys in order to overwhelm their defenses. Wolfpack tactics were only possible if the submarines in the wolfpack could receive instructions by radio on where to assemble in the vast ocean, and where and when to strike. The German U-boat force had to rely very strongly on Enigma to ensure the British could not listen in on German radio traffic. If the British could successfully read Enigma, they could use the messages to divert convoys from traps, and trap U-boats in turn.
Bletchley Park was able to penetrate German Navy Enigma to a limited extent by a process of "gardening" cribs. British Royal Air Force aircraft would drop mines in the sea in locations where the Germans were able to spot the drops. The Germans would send out a warning, and Bletchley Park would be able to use the coordinates of the mines as cribs to crack messages. However, this was too hit-or-miss to be useful as a regular practice. The British therefore turned to a more direct way of obtaining German Navy daykeys: stealing codebooks.
The most daring of these "pinches" took place in May 1941, when the U-boat U-110 was forced to the surface by British Royal Navy convoy escorts. The U-110's crew abandoned ship after leaving scuttling charges, but they failed to detonate. The submarine's captain, U-boat "ace" Julius Lemp, was apparently shot by the British when he tried to return to the vessel.
When the submarine failed to go to the bottom, Royal Navy Sublieutenant David Baum of the HMS BULLDOG went down the hatch to investigate. Baum found conditions on board the submarine to be as safe as was consistent with the fact that it had been damaged and abandoned, and a human chain was formed to get the valuable codebooks and equipment onto a destroyer for safekeeping. The U-110 went down under tow. The British announced that the U-110 had been sunk, and went to lengths to convince the survivors that it had done so quickly.
One junior member of the British intelligence community came up with a number of wild schemes for pinching codebooks, such as having an aircrew of German-speaking British ditch a captured Luftwaffe bomber near a German cargo vessel, and then take over the ship when they were rescued. His name was Ian Fleming, a stockbroker in his previous life. His schemes came to little in the real world -- field operators were unimpressed with Fleming, judging him a headquarters type who liked the good life -- but he would go on after the war to use them to make a fortune from a series of novels about James Bond, Agent 007. Despite Fleming's intelligence career, his books were not noted for their authenticity.
* The captured codebooks gave the British a significant advantage in the Battle of the Atlantic until 1 February 1942, when the Germans changed the cipher scheme again, introducing a new Enigma that featured a special fourth rotor. The fourth rotor could be set so that the new Enigma acted as a three-rotor machine, allowing U-boats to receive new Enigma machines sequentially, not going to four-rotor operation until the entire fleet was up to standard. However, in December a U-boat radio operator had made a blunder, sending a message using four-rotor operation. When he realized his mistake, he then retransmitted the same message in three-rotor mode. The British caught it and figured out the wiring of the fourth rotor.

Just figuring out the rotor wiring wasn't enough. The Germans also adopted new codebooks, and the fourth rotor meant that new bombes had to be designed and built. The real breakthrough on the new naval Engima didn't take place until 30 October 1942, when the Royal Navy attacked the U-559 in the Mediterranean off the coast of Egypt and forced it to the surface, with the crew abandoning ship. Three crewmen from the HMS PETARD -- Anthony Fasson, Colin Grazier, and Tommy Brown -- boarded the foundering submarine and managed to get out vital codebooks before it went down, taking Fasson and Grazier with it.
By mid-December 1942, Bletchley Park was reading naval Enigma traffic. It turned out that when the Germans sent their daily weather reports, they put the four-rotor Enigma into three-rotor operation -- and then retained the same setup for the three rotors when they went back to four-rotor operation. That meant that all the British had to do was check the 26 positions of the fourth rotor. They were able to read Enigma traffic for a few months, but in March 1943, the Germans changed the cipher scheme again. However, the Bletchley Park group, having obtained a handhold on the procedures, was able to crack the new naval Enigma in a month.
Although the Battle of the Atlantic was reaching a climax at that time, with massive losses of Allied shipping, the Allied net of antisubmarine measures, including ever stronger sea and air patrols, improved tactics, radio direction finding, radar, and decrypts finally closed around the Germans, and by the late spring of 1943, the U-boats were taking unacceptable losses. The Allies had won the Battle of the Atlantic, though the struggle against the U-boats would continue at a lower level for the rest of the war, with the Germans at a grave disadvantage.
* The four-rotor Enigma led to frictions with the Americans. In early 1942 the US Navy, impatient with British efforts on building four-rotor bombes, contacted the National Cash Register (NCR) company to build the device -- incidentally, the fact that the Navy was working on the construction of bombes at that time deflates the notion that the British concealed their Enigma work from the US. In any case, the British were not happy with this, feeling it was a duplication of effort and a violation of the arrangement between the codebreaking organizations of the two nations, but the US Navy felt they needed the capability and that the British were not making adequate progress on building their own four-rotor bombes. Turing visited the US in December 1942, and came back with an irritated report on the American activities.
In fact, although the British did build four-rotor bombes, in practice BTM had their hands full building the older three-rotor bombes for German Army and Luftwaffe communications. Gradually the British accepted the American work on four-rotor bombes, with the US providing a number to Britain.
* The Germans didn't learn that Enigma had been cracked until long after the war. Doenitz worried that there was a spy among his people who was reporting the positions of his submarines. The idea that the British had cracked Enigma was considered, and rejected as impossible.
The triumph of Bletchley Park over German naval Enigma and the U-boats was tarnished by the fact that the British had handed many of the convoys to the U-boats on a platter in the first place. The Allies proved very competent at cracking German codes, but not entirely competent at protecting their own. The German naval intelligence organization, the "B-Dienst", one of the smallest but most competent of the uncoordinated patchwork of German cryptographic organizations, was able to crack convoy codes in 1941 and 1942, with disastrous consequences for the Allies.
In the spring of 1943, after Bletchley Park managed to crack naval Enigma again, some Enigma intercepts revealed a suspiciously detailed knowledge of convoy details and movements. Comparison with convoy code messages showed them to be effective copies; in June 1943, a new and stronger convoy code scheme was introduced, and the Germans were not able to penetrate it again.
* British and American cooperation on codebreaking had been moving ahead in the meantime. In April 1943, Friedman and two US Army officers, Colonel Alfred McCormack and Colonel Telford Taylor paid a two-month visit to Britain for discussions. The exercise led to the signing of the "Britain-USA (BRUSA) Agreement" on 17 May 1943. The BRUSA Agreement established an interlocking arrangement between the codebreaking and radio intercept organizations of the two countries that provided for exchange of personnel, joint regulations for the handling of the supersensitive material, and methods for its distribution.
The BRUSA Agreement led to conferences that not only involved the US and the UK, but also the cryptological organizations of Canada and Australia. At the second Joint Allied Conference, held at the Army SIS site at Arlington Hall in Arlington, Virginia, on 13 March 1944 35 representatives of senior crypto staff from the US, the UK, Canada, and Australia met in one of the most secret conferences of the war. By the end of the conflict, the codebreaking organizations of the English-speaking nations formed a closely-linked and highly cooperative network.
In 1947, BRUSA was superseded by the five-power "UKUSA" agreement. Its details are still secret, but apparently it established the United States as a first party to the treaty, and Britain, Canada, and Australia-New Zealand as second parties. NATO nations and such other nations as Japan and Korea later signed on as third parties. Among the first and second parties there is a general agreement not to restrict data, but with the third parties the sharing was more restricted. The UKUSA arrangement remains in effect.
BACK_TO_TOP* The story of what ULTRA bought the Allies was revealed in 1974 when Fred Winterbotham, a senior field officer of the British SIS, published his memoirs of the war under the title of THE ULTRA SECRET.
Winterbotham had been in charge of distributing ULTRA intelligence to army commanders in the field. Although naval intelligence was passed directly onto the Admiralty, which handled its own intelligence distribution, army commanders received the intelligence through military "special liaison unit (SLU)" teams, which were Winterbotham's domain. The SLU teams provided the information only to senior officers and only on a "need to know" basis. Field commanders could not use the intelligence without devising a "cover plan" to mislead the Germans as to the source of the information.
While Winterbotham did not reveal and likely did not know much about the technical aspects of the Bletchley Park operation, he gave a stunning account of how ULTRA intelligence had given the Allies a step ahead in the Battle of Britain, the battles for North Africa, Sicily, Italy, and France, and a remarkable list of other military actions. Historians generally agree that the Allies had a consistent level of military intelligence on the intent and actions of the Axis that was unsurpassed in history.
The fact that the British had cracked Enigma remained classified until Winterbotham published THE ULTRA SECRET. Ironically, ULTRA was no secret to the Soviet Union, Britain's principal adversary in the postwar period. The British occasionally passed ULTRA information on to Josef Stalin, filtered through the British military mission in Moscow, with the operation codenamed VULTURE. Stalin accepted such leads with puzzling indifference, and it wasn't until years later that the British found that one of the Bletchley Park workers, John Cairncross, was a Red spy, having been recruited by Soviet intelligence at Cambridge before he joined the British military. He was eventually awarded the Hero of the Soviet Union medal in secret. Stalin knew a great deal about ULTRA.
While the Soviets were aware of ULTRA, to others the publication of THE ULTRA SECRET was a bombshell. Marian Rejewski was startled to find out just how important his prewar work on Enigma had been. Karl Doenitz was thunderstruck to find out that the British had been reading the "unbreakable" Enigma cipher through most of the war.
The knowledge came too late for some, most particularly for Alan Turing. Turing was gay, and he suffered harassment at the hands of the law over the matter after the war. He died of poisoning in 1954 at age 42; it is generally thought he committed suicide, but what actually happened was unclear. He left no note, he seemed cheerful enough to those around him, and he may have accidentally poisoned himself tinkering with chemicals at home; he liked to experiment, and he was known to be sloppy in his procedures. Turing has become something of a heroic gay icon in modern times, but in a document focused on cryptography the issue of his sexual orientation seems irrelevant. What is relevant is the fact that he was a genius.
BACK_TO_TOP